Federating via OAuth¶
The Slices portal is a standards-compliant OAuth2 and OpenID Connect provider. It allows Clients (also known as Relying Parties) to verify the identity of the End-User, as well as to obtain basic profile information about the End-User in a REST-like manner.
OpenID Connect extends OAuth 2.0. The OAuth2.0 protocol provides API security via scoped access tokens, and OpenID Connect provides user authentication and single sign-on (SSO) functionality.
The Slices portal provides all OpenID Connect metadata via https://portal.slices-sc.eu/.well-known/openid-configuration.
The access_token and id_token returned by the OIDC login flow are JWT tokens containing information on the end user. The JWKS containing the keys to verify these tokens can also be retrieved via the metadata linked above.
Registering your service as an OAuth Client¶
Please email helpdesk@ilabt.imec.be with the following information on your service:
- Service Name
- Service URL
- One or more redirect URI’s: valid callback locations where the authorization code or tokens should be sent to. (Tip: also include any redirect URI’s that you want to use for your test and/or staging environments.)
- Token endpoint auth method: either
client_secret_basicorclient_secret_postare supported.
We will then register your service in the portal and provide you with a client_id and client_secret to use.
Familiarizing yourself with the authentication workflow¶
If you want to familiarize yourself with the OIDC workflow, you can use either the Open ID Connect Playground or Hoppscotch.
Note that the provided Client ID and Client Secret only have https://openidconnect.net/callback and https://hoppscotch.io as a registered redirect URI. They can thus only be used on these websites.
OpenID Connect Playground¶
- Click on the ‘Configuration’ button
- Select Server Template ‘Custom’
- Use Discovery Document URL https://portal.slices-sc.eu/.well-known/openid-configuration
- Set the OIDC Client ID to
zjscm8rJBH7j96y5sUeVF5svand OIDC Client Secret toPEesNzJRtjXLoGlL0XVFWDFRmAIHrywB3fRh6EKebBHKepZV - Set Scope to openid userinfo
- Save the configuration
You can now perform the full authentication flow:
- Redirect to OpenID Connect Server
- Exchange Code from Token
- Verify User Token
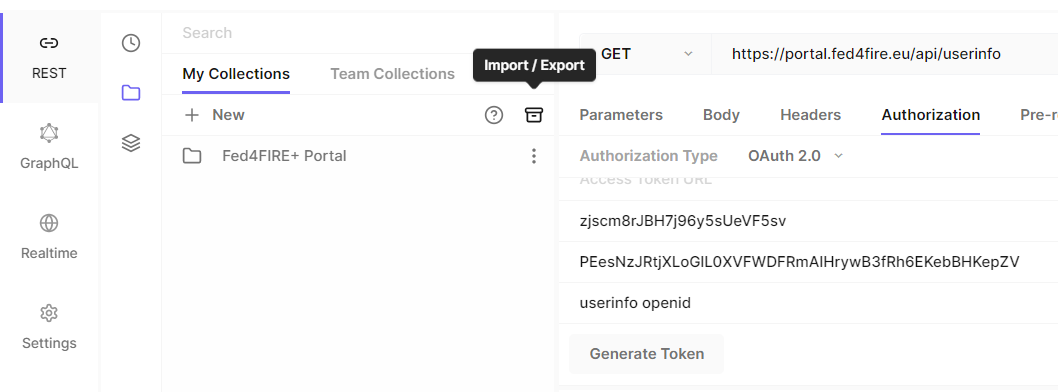
Hoppscotch¶
Download the Slices Portal Hoppscotch collection with the example userinfo request.
On hoppscotch.io:
- Load the Collection via ‘My Collections’ -> ‘Import/Export’ -> ‘Import from Hoppscotch’
- Open the ‘Userinfo request’ in this collection
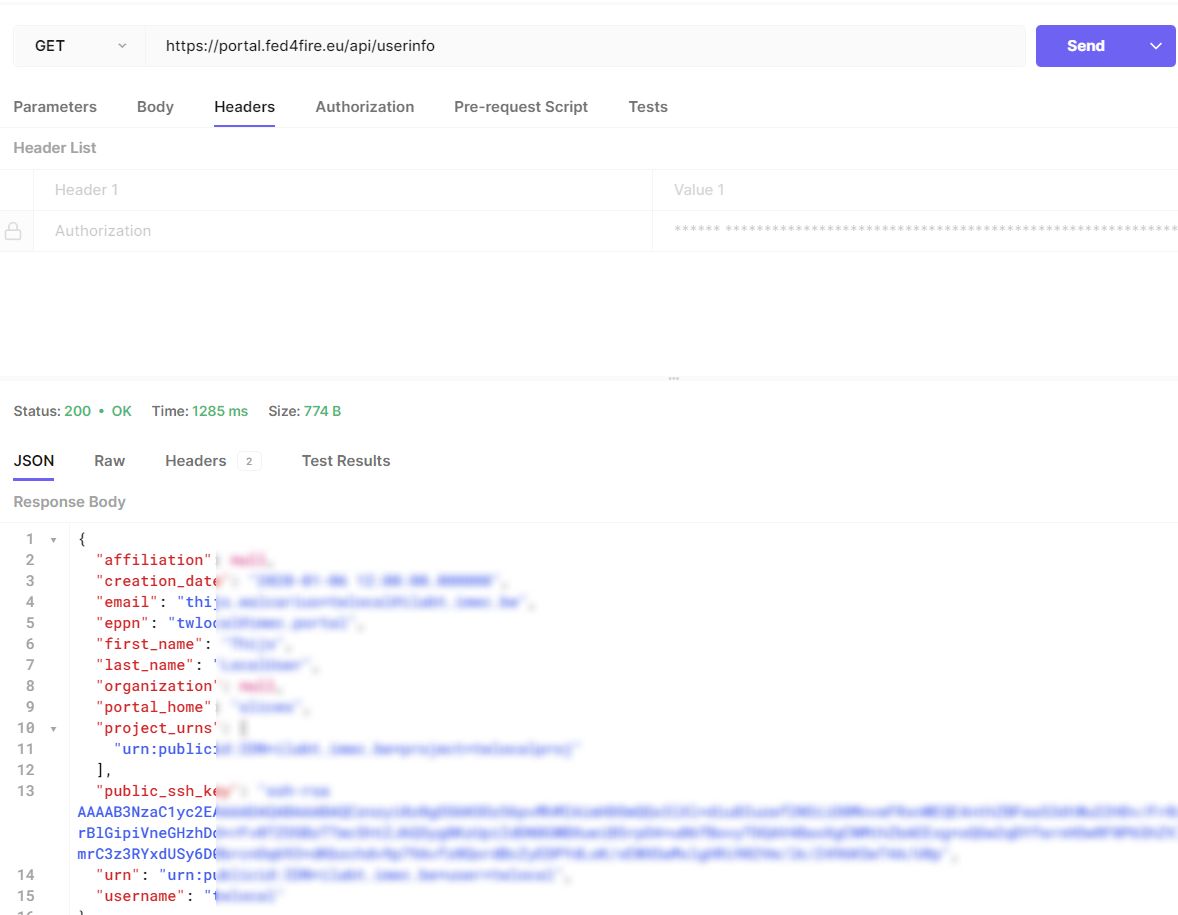
- In the tab Authorization, scroll down and click on ‘Generate token’ to perform the OIDC login flow
- Now you can execute the request itself, which will pass on the retrieved access_token in the Authorization header when querying https://portal.slices-sc.eu/api/userinfo.